What is the key space of an affine cipher?
The key space of an affine cipher is a fundamental concept in the study of classical cryptography, particularly within the domain of modular arithmetic and historical ciphers. Understanding the key space involves comprehending the range of possible keys that can be used within the affine cipher algorithm to encrypt and decrypt messages. The affine cipher is a type of monoalphabetic substitution cipher, which means each letter in the plaintext is mapped to a corresponding letter in the ciphertext by a mathematical function. The function used in an affine cipher is of the form:
![]()
where:
– ![]() is the encryption function.
is the encryption function.
– ![]() is the numerical value of the plaintext letter.
is the numerical value of the plaintext letter.
– ![]() and
and ![]() are the keys of the cipher.
are the keys of the cipher.
– ![]() is the size of the alphabet.
is the size of the alphabet.
To decrypt the ciphertext, the inverse function is used:
![]()
where:
– ![]() is the decryption function.
is the decryption function.
– ![]() is the numerical value of the ciphertext letter.
is the numerical value of the ciphertext letter.
– ![]() is the modular multiplicative inverse of
is the modular multiplicative inverse of ![]() modulo
modulo ![]() .
.
The key space of the affine cipher is determined by the values of ![]() and
and ![]() . For the affine cipher to be a valid encryption method,
. For the affine cipher to be a valid encryption method, ![]() must be coprime with
must be coprime with ![]() , meaning that
, meaning that ![]() , where
, where ![]() stands for the greatest common divisor. This requirement ensures that
stands for the greatest common divisor. This requirement ensures that ![]() has a modular multiplicative inverse, which is necessary for the decryption process.
has a modular multiplicative inverse, which is necessary for the decryption process.
Detailed Analysis of Key Space
Determining Valid Values for 
The first step in understanding the key space is to determine the valid values for ![]() . Since
. Since ![]() must be coprime with
must be coprime with ![]() , we need to count the number of integers between 1 and
, we need to count the number of integers between 1 and ![]() that are coprime with
that are coprime with ![]() . This count is given by Euler's Totient Function
. This count is given by Euler's Totient Function ![]() . For example, if
. For example, if ![]() (which is the size of the English alphabet), the values of
(which is the size of the English alphabet), the values of ![]() must be coprime with 26. The integers coprime with 26 are:
must be coprime with 26. The integers coprime with 26 are:
![]()
Thus, there are 12 possible values for ![]() when
when ![]() .
.
Determining Valid Values for 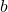
The value of ![]() can be any integer between 0 and
can be any integer between 0 and ![]() . For
. For ![]() , this gives us 26 possible values for
, this gives us 26 possible values for ![]() :
:
![]()
Calculating the Total Key Space
The total key space is the product of the number of valid values for ![]() and the number of valid values for
and the number of valid values for ![]() . Using the example where
. Using the example where ![]() :
:
![]()
Therefore, the affine cipher with an alphabet size of 26 has a key space of 312 possible keys.
Example of Affine Cipher Encryption and Decryption
To illustrate the process of encryption and decryption using the affine cipher, let us consider an example with specific values for ![]() and
and ![]() .
.
Encryption Example
Let:
– ![]()
– ![]()
– ![]()
The encryption function is:
![]()
Suppose we want to encrypt the plaintext letter 'H'. First, we convert 'H' to its numerical equivalent, which is 7 (assuming 'A' = 0, 'B' = 1, …, 'H' = 7).
![]()
The numerical value 17 corresponds to the letter 'R' in the alphabet. Thus, the plaintext letter 'H' is encrypted as 'R'.
Decryption Example
To decrypt the ciphertext letter 'R', we need to use the decryption function. First, we find the modular multiplicative inverse of ![]() modulo
modulo ![]() . The modular multiplicative inverse of 5 modulo 26 is the integer
. The modular multiplicative inverse of 5 modulo 26 is the integer ![]() such that:
such that:
![]()
Using the Extended Euclidean Algorithm, we find that the modular multiplicative inverse of 5 modulo 26 is 21. Thus, the decryption function is:
![]()
Converting 'R' back to its numerical equivalent, which is 17:
![]()
The numerical value 7 corresponds to the letter 'H' in the alphabet. Thus, the ciphertext letter 'R' is decrypted back to 'H'.
Practical Considerations and Security
While the affine cipher provides a straightforward example of classical encryption using modular arithmetic, it is important to note that it is not secure by modern standards. The key space of 312 possible keys is relatively small, making it vulnerable to brute-force attacks. Additionally, the affine cipher is a type of monoalphabetic substitution cipher, which means it does not provide sufficient complexity to resist frequency analysis attacks. Each letter in the plaintext is mapped to a unique letter in the ciphertext, preserving the frequency distribution of the letters.
In practical terms, the affine cipher is primarily of historical and educational interest. It serves as an excellent example to illustrate the principles of modular arithmetic and the concept of key space in cryptography. However, for secure communication, modern cryptographic algorithms such as the Advanced Encryption Standard (AES) or the RSA algorithm are used, which provide significantly larger key spaces and enhanced security features.
The key space of an affine cipher is determined by the number of valid values for the keys ![]() and
and ![]() , where
, where ![]() must be coprime with the size of the alphabet
must be coprime with the size of the alphabet ![]() , and
, and ![]() can be any integer within the range of the alphabet size. For an alphabet size of 26, the key space consists of 312 possible keys. While the affine cipher is not secure by modern standards, it provides valuable insights into the principles of classical cryptography and modular arithmetic.
can be any integer within the range of the alphabet size. For an alphabet size of 26, the key space consists of 312 possible keys. While the affine cipher is not secure by modern standards, it provides valuable insights into the principles of classical cryptography and modular arithmetic.
Other recent questions and answers regarding EITC/IS/CCF Classical Cryptography Fundamentals:
- Is cryptography considered a part of cryptology and cryptanalysis?
- Will a shift cipher with a key equal to 4 replace the letter d with the letter h in ciphertext?
- Does the ECB mode breaks large input plaintext into subsequent blocks
- Do identical plaintext map to identical cipher text of a letter frequency analysis attact against a substitution cipher
- What is EEA ?
- Are brute force attack always an exhausive key search?
- In RSA cipher, does Alice need Bob’s public key to encrypt a message to Bob?
- Can we use a block cipher to build a hash function or MAC?
- What are initialization vectors?
- How many part does a public and private key has in RSA cipher
View more questions and answers in EITC/IS/CCF Classical Cryptography Fundamentals

